
ETSI GR ZSM 015
V1.1.1 (2024-02)
Zero
-
touch network and Service Management (ZSM);
Network Digital Twin
Disclaimer
The present document has been produced and approved by the Zero-touch network and Service Management (ZSM) ETSI
Industry Specification Group (ISG) and represents the views of those members who participated in this ISG.
It does not necessarily represent the views of the entire ETSI membership.
GROUP REPORT

ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
2
Reference
DGR/ZSM-015_NDT
Keywords
automation, Digital Twins, network management
ETSI
650 Route des Lucioles
F-06921 Sophia Antipolis Cedex - FRANCE
Tel.: +33 4 92 94 42 00 Fax: +33 4 93 65 47 16
Siret N° 348 623 562 00017 - APE 7112B
Association à but non lucratif enregistrée à la
Sous-Préfecture de Grasse (06) N° w061004871
Important notice
The present document can be downloaded from:
https://www.etsi.org/standards-search
The present document may be made available in electronic versions and/or in print. The content of any electronic and/or
print versions of the present document shall not be modified without the prior written authorization of ETSI. In case of any
existing or perceived difference in contents between such versions and/or in print, the prevailing version of an ETSI
deliverable is the one made publicly available in PDF format at www.etsi.org/deliver.
Users of the present document should be aware that the document may be subject to revision or change of status.
Information on the current status of this and other ETSI documents is available at
https://portal.etsi.org/TB/ETSIDeliverableStatus.aspx
If you find errors in the present document, please send your comment to one of the following services:
https://portal.etsi.org/People/CommiteeSupportStaff.aspx
If you find a security vulnerability in the present document, please report it through our
Coordinated Vulnerability Disclosure Program:
https://www.etsi.org/standards/coordinated-vulnerability-disclosure
Notice of disclaimer & limitation of liability
The information provided in the present deliverable is directed solely to professionals who have the appropriate degree of
experience to understand and interpret its content in accordance with generally accepted engineering or
other professional standard and applicable regulations.
No recommendation as to products and services or vendors is made or should be implied.
No representation or warranty is made that this deliverable is technically accurate or sufficient or conforms to any law
and/or governmental
rule and/or regulation and further, no representation or warranty is made of merchantability or fitness
for any particular purpose or against infringement of intellectual property rights.
In no event shall ETSI be held liable for loss of profits or any other incidental or consequential damages.
Any software contained in this deliverable is provided "AS IS" with no warranties, express or implied, including but not
limited to, the warranties of merchantability, fitness for a particular purpose and non-infringement of intellectual property
rights and ETSI shall not be held liable in any event for any damages whatsoever (including, without limitation, damages
for loss of profits, business interruption, loss of information, or any other pecuniary loss) arising
out of or related to the use
of or inability to use the software.
Copyright Notification
No part may be reproduced or utilized in any form or by any means, electronic or mechanical, including photocopying and
microfilm except as authorized by written permission of ETSI.
The content of the PDF version shall not be modified without the written authorization of ETSI.
The copyright and the foregoing restriction extend to reproduction in all media.
© ETSI 2024.
All rights reserved.

ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
3
Contents
Intellectual Property Rights ................................................................................................................................ 5
Foreword ............................................................................................................................................................. 5
Modal verbs terminology .................................................................................................................................... 5
1 Scope ........................................................................................................................................................ 6
2 References ................................................................................................................................................ 6
2.1 Normative references ......................................................................................................................................... 6
2.2 Informative references ........................................................................................................................................ 6
3 Definition of terms, symbols and abbreviations ....................................................................................... 7
3.1 Terms .................................................................................................................................................................. 7
3.2 Symbols .............................................................................................................................................................. 8
3.3 Abbreviations ..................................................................................................................................................... 8
4 Introduction of Network Digital Twin ..................................................................................................... 9
4.1 Concept of Network Digital Twin ...................................................................................................................... 9
4.1.1 Introduction................................................................................................................................................... 9
4.1.2 Examples of NDT Taxonomy ..................................................................................................................... 10
4.2 Generic benefits of Network Digital Twin ....................................................................................................... 10
4.3 Emulation, Simulation and Modelling Time .................................................................................................... 11
4.4 Industry progress of Digital Twin .................................................................................................................... 12
4.4.1 Introduction................................................................................................................................................. 12
4.4.2 Digital Twin Industrial progress ................................................................................................................. 12
4.4.3 Standardization of the Network Digital Twin ............................................................................................. 13
4.4.4 Synergies between Industrial DT and NDT ................................................................................................ 13
5 Examples of use cases using NDT ......................................................................................................... 14
5.1 Radio network energy saving ........................................................................................................................... 14
5.1.1 Description .................................................................................................................................................. 14
5.1.2 Use case details ........................................................................................................................................... 14
5.2 Network Slicing risk prediction ........................................................................................................................ 14
5.2.1 Description .................................................................................................................................................. 14
5.2.2 Use case details ........................................................................................................................................... 15
5.3 Signalling storm simulation and analysis ......................................................................................................... 16
5.3.1 Description .................................................................................................................................................. 16
5.3.2 Use case details ........................................................................................................................................... 16
5.4 Machine Learning Training .............................................................................................................................. 17
5.4.1 Description .................................................................................................................................................. 17
5.4.2 Use case details ........................................................................................................................................... 17
5.5 DevOps-Oriented Certification ........................................................................................................................ 17
5.5.1 Description .................................................................................................................................................. 17
5.5.2 Use case details ........................................................................................................................................... 18
5.6 ML inference-impact emulation ....................................................................................................................... 18
5.6.1 Description .................................................................................................................................................. 18
5.6.2 Use case details ........................................................................................................................................... 18
5.7 A QoT-Oriented NDT for Optical Networks.................................................................................................... 19
5.8 Network Playback to perform historical incident analysis ............................................................................... 20
5.8.1 Description .................................................................................................................................................. 20
5.8.2 Use case details ........................................................................................................................................... 20
5.9 Data generation for NDT .................................................................................................................................. 21
5.9.1 Description .................................................................................................................................................. 21
5.9.2 Use case details ........................................................................................................................................... 21
5.10 NDT resource management and orchestration ................................................................................................. 21
5.10.1 Description .................................................................................................................................................. 21
5.10.2 Use case details ........................................................................................................................................... 22
5.11 NDT Time Management .................................................................................................................................. 23
5.11.1 Description .................................................................................................................................................. 23
5.12 NDT consumer preference ............................................................................................................................... 24
ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
4
5.12.1 Description .................................................................................................................................................. 24
5.12.2 Use case details ........................................................................................................................................... 25
5.13 NDT Fault Injection Analysis .......................................................................................................................... 25
5.13.1 Description .................................................................................................................................................. 25
5.13.2 Use case details ........................................................................................................................................... 25
5.14 NDT data accuracy ........................................................................................................................................... 26
5.14.1 Description .................................................................................................................................................. 26
5.14.2 Use case details ........................................................................................................................................... 26
6 NDT for zero-touch Network and Service management ........................................................................ 27
6.1 Principles .......................................................................................................................................................... 27
6.2 NDT Mapping to ZSM Architecture ................................................................................................................ 29
6.2.1 Analyzing NDT .......................................................................................................................................... 29
6.2.2 Controlling NDT ......................................................................................................................................... 30
6.3 Potential new ZSM Framework Capabilities to support the NDT .................................................................... 30
6.3.1 Generic Capabilities .................................................................................................................................... 30
6.3.2 Data collection ............................................................................................................................................ 31
6.3.3 Data Generation .......................................................................................................................................... 31
6.3.4 Historical capabilities ................................................................................................................................. 31
6.3.5 NDT ML inference-impact emulation ........................................................................................................ 32
6.3.6 NDT resource orchestration capabilities ..................................................................................................... 32
6.3.7 NDT Time Management Capabilities ......................................................................................................... 32
6.3.8 NDT consumer preference capabilities ....................................................................................................... 33
6.3.9 NDT Fault injection capabilities ................................................................................................................. 33
6.3.10 NDT data accuracy capabilities .................................................................................................................. 33
Annex A (informative): Change history ............................................................................................... 34
History .............................................................................................................................................................. 36

ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
5
Intellectual Property Rights
Essential patents
IPRs essential or potentially essential to normative deliverables may have been declared to ETSI. The declarations
pertaining to these essential IPRs, if any, are publicly available for ETSI members and non-members, and can be
found in ETSI SR 000 314: "Intellectual Property Rights (IPRs); Essential, or potentially Essential, IPRs notified to
ETSI in respect of ETSI standards", which is available from the ETSI Secretariat. Latest updates are available on the
ETSI Web server (https://ipr.etsi.org/).
Pursuant to the ETSI Directives including the ETSI IPR Policy, no investigation regarding the essentiality of IPRs,
including IPR searches, has been carried out by ETSI. No guarantee can be given as to the existence of other IPRs not
referenced in ETSI SR 000 314 (or the updates on the ETSI Web server) which are, or may be, or may become,
essential to the present document.
Trademarks
The present document may include trademarks and/or tradenames which are asserted and/or registered by their owners.
ETSI claims no ownership of these except for any which are indicated as being the property of ETSI, and conveys no
right to use or reproduce any trademark and/or tradename. Mention of those trademarks in the present document does
not constitute an endorsement by ETSI of products, services or organizations associated with those trademarks.
DECT™, PLUGTESTS™, UMTS™ and the ETSI logo are trademarks of ETSI registered for the benefit of its
Members. 3GPP™
and LTE™ are trademarks of ETSI registered for the benefit of its Members and of the 3GPP
Organizational Partners. oneM2M™ logo is a trademark of ETSI registered for the benefit of its Members and of the
oneM2M Partners. GSM
®
and the GSM logo are trademarks registered and owned by the GSM Association.
Foreword
This Group Report (GR) has been produced by ETSI Industry Specification Group (ISG) Zero-touch network and
Service Management (ZSM).
Modal verbs terminology
In the present document "should", "should not", "may", "need not", "will", "will not", "can" and "cannot" are to be
interpreted as described in clause 3.2 of the ETSI Drafting Rules (Verbal forms for the expression of provisions).
"must" and "must not" are NOT allowed in ETSI deliverables except when used in direct citation.

ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
6
1 Scope
The present document describes the Network Digital Twin concept, investigates its applicability for automation of zero-
touch network and service management and introduces existing, emerging and future scenarios that can benefit from it.
Principles and functionality needed to support and utilize the Network Digital Twin for zero-touch network and service
management is introduced, considering also state of the art.
The present document outlines recommendations of additional capabilities needed in the ZSM framework to support
Network Digital Twins.
The present document identifies existing specifications and solutions (both ETSI and external ones) that can be
leveraged to maximize synergies. Collaboration with other SDOs (e.g. in IRTF NMRG, ITU-T SG13) are recommended
when appropriate.
2 References
2.1 Normative references
Normative references are not applicable in the present document.
2.2 Informative references
References are either specific (identified by date of publication and/or edition number or version number) or
non-specific. For specific references, only the cited version applies. For non-specific references, the latest version of the
referenced document (including any amendments) applies.
NOTE: While any hyperlinks included in this clause were valid at the time of publication, ETSI cannot guarantee
their long term validity.
The following referenced documents are not necessary for the application of the present document but they assist the
user with regard to a particular subject area.
[i.1] A. M. Madni, C. C. Madni and S. D. Lucero: "Leveraging digital twin technology in model-based
systems engineering", MDPI Systems, vol. 7, no. 7; doi:10.3390/systems7010007, 2019.
[i.2] Y. Wu, K. Zhang and Y. Zhang: "Digital Twin Networks: A Survey", IEEE Internet of Things J.,
vol. 8, no. 18, pp. 13789-13804, September 2021.
[i.3] draft-irtf-nmrg-network-digital-twin-arch: "Digital Twin Network: Concepts and Architecture", C.
Zhou, H. Yang, D. Lopez, A. Pastor, Q. Wu, M. Boucadair, C. Jacquenet.
[i.4] ETSI GS ZSM 007: "Zero-touch network and Service Management (ZSM); Terminology for
concepts in ZSM".
[i.5] ETSI GS ZSM 003: "Zero-touch network and Service Management (ZSM); End-to-end
management and orchestration of network slicing".
[i.6] ETSI GS ZSM 002: "Zero-touch network and Service Management (ZSM); Reference
Architecture".
[i.7] Recommendation ITU-T Y.3090: "Digital twin network - Requirements and architecture".
[i.8] draft-chen-nmrg-dtn-interface: "Requirements for Interfaces of Network Digital Twin", D. Chen,
H. Yang, C. Zhou, March 2023.
[i.9] draft-paillisse-nmrg-performance-digital-twin-01: "Performance-Oriented Digital Twins for Packet
and Optical Networks", J. Paillisse, P. Almasan, M. Ferriol, P. Barlet, A. Cabellos, S. Xiao, X. Shi,
X. Cheng, C. Janz, A. Guo, D. Perino, D. Lopez, A. Pastor, April 2023.

ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
7
[i.10] draft-yz-nmrg-dtn-flow-simulation-01: "Digital Twin Network Flow Simulation", H. Yang, C.
Zhou, April 2023.
[i.11] draft-yc-nmrg-dtn-owd-measurement-01: "One-way delay measurement method based on Digital
Twin Network", H. Yang, D. Chen, April 2023.
[i.12] C. Janz, Y. You, M. Hemmati, Z. Jiang, A. Javadtalab, J. Mitra: "Digital Twin for the Optical
Network: Key Technologies and Enabled Automation Applications", IEEE/IFIP International
Workshop on Technologies for Network Twins, Budapest, Hungary, April 2022.
[i.13] ETSI GS ZSM 012: "Zero-touch network and Service Management (ZSM); Enablers for Artificial
Intelligence-based Network and Service Automation".
[i.14] ISO 23247 series (2021): ""Automation systems and integration -- Digital twin framework for
manufacturing".
[i.15] IEC 62832-2 (2020): "Industrial-process measurement, control and automation - Digital factory
framework - Part 2: Model elements".
[i.16] IEEE 1451™: "Standard for a Smart Transducer Interface for Sensors and Actuators - Common
Functions, Communication Protocols, and Transducer Electronic Data Sheet (TEDS) Formats".
[i.17] IEEE 2888™ series.
[i.18] IEEE P2888.1™: "Specification of Sensor Interface for Cyber and Physical World".
[i.19] IEEE P2888.2™: "Standard for Actuator Interface for Cyber and Physical World".
[i.20] IEEE P2806.1™: "Standard for Connectivity Requirements of Digital Representation for Physical
Objects in Factory Environments".
[i.21] IEEE 2888.3™: "Orchestration of Digital Synchronization between Cyber and Physical World.
document".
[i.22] ISO/IEC AWI 30172:" Digital Twin : Use Cases".
[i.23] ISO/IEC AWI 30173: "Digital Twin : Concepts And Terminology".
3 Definition of terms, symbols and abbreviations
3.1 Terms
For the purposes of the present document, the terms given in ETSI GS ZSM 007 [i.4] and the following apply:
data drift: change in observed behaviour of the physical twin, as manifested in observed data or data patterns,
suggesting that performance of NDT models may be degraded
NOTE: Examples for data patterns are peak hour KPI, traffic distribution, user distribution, workday, weekend
patterns etc.
digital twin: digital counterpart of the physical twin that captures its attributes, behaviour and interactions
NOTE: In the context of the present document the digital twin is referred as the Network Digital Twin (or NDT).
input data accuracy: accuracy of the input data used for the NDT model compared with the corresponding behaviour
of the physical twin at the same time as related to the NDT virtual time
NDT master virtual clock: NDT virtual clock that provides virtual time reference for synchronizing a set of NDT
virtual clocks
NDT time delay: time delay that specifies the delay associated with data collection from the physical twin and
processing of the same data in the NDT
ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
8
NDT virtual clock: clock that provides NDT virtual time
NDT virtual time: time used by the NDT MnS
NOTE: NDT virtual time is artificial time used in NDT modelling, simulation or emulation
output data accuracy: accuracy of the NDT output data compared with the corresponding behaviour observed in the
physical twin at the same time as related to the NDT virtual time
physical twin: object, system, process, software or environment that the digital twin is designed to replicate and
represent virtually
NOTE: In the context of the present document the physical twin is a communications network, or some part of
one, including e.g. physical network elements and components, virtualized network functions (VNFs - i.e.
network functional elements instantiated as software-based entities), the physical hosts for such VNFs,
services and traffic, etc.
twinning: process that creates and maintains a digital twin corresponding to a particular physical twin
NOTE 1: In the context of the present document twinning is the process that creates and maintains the NDT.
NOTE 2: Maintain means ongoing actions that are taken to keep the digital twin aligned (or 'twinned') to the
physical twin.
3.2 Symbols
Void.
3.3 Abbreviations
For the purposes of the present document, the abbreviations given in ETSI GS ZSM 007 [i.4] and the following apply:
AN Access Network
C-Plane Control Plane
CN Core Network
GAN Generative Adversarial Network
M-Plane Management Plane
NDT Network Digital Twin
TN Transport Network
U-Plane User Plane

ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
9
4 Introduction of Network Digital Twin
4.1 Concept of Network Digital Twin
4.1.1 Introduction
Digital Twins (DTs) are an increasingly examined technology relevant to system automation. A DT is a virtual replica
of a real-world system - a "physical" system - on which operations can be performed [i.1]. The observed outcomes and
effects of such operations constitute information that can be used e.g. to inform operational decision-making, including
within automation-supporting closed loops.
A Network Digital Twin (NDT) is a DT whose physical counterpart is a communications network, or some part of one
[i.2]. The communications network can include e.g. physical network elements and components, virtualized network
functions (VNFs - i.e. network functional elements instantiated as software-based entities), the physical hosts for such
VNFs, services and traffic, etc.
In [i.3], it is proposed that an NDT encompasses four components: data, models, interfaces and mapping (referring to
between digital entities and their real-world counterparts). Data and models constitute the functional core of an NDT.
"Data" can include information about the network, its use, and its environment; e.g.:
• physical and virtual equipment types, functions and capabilities;
• network topology and configuration;
• services or traffic;
• network element, or network element component, health and status (e.g. fault management data);
• service or network element performance data;
• network environmental data;
• interface-related information, including interface operations;
• histories of any or all of the above;
• etc.
Specific data consumed by an NDT is determined by the requirements of targeted use cases.
"Models" can include information and data models used to represent e.g. network or service topology or configuration,
and also behavioural models used to compute the physical network, service or other behaviours expected in postulated
scenarios. Specifics of required models, including the required accuracies of behavioural models, are determined by the
requirements of targeted use cases.
The functional perimeter of an NDT can be viewed as limited to the information-generating function: an "Analyzing
NDT". Alternatively, it can be viewed as the information-generating function and encompassing other functions, such
as additional closed loop stages, that are needed to drive actions on the physical twin: a "Controlling NDT".
An Analyzing NDT can be used to determine the expected behavioural impacts of changes to network, traffic, service,
environmental or other conditions, or of prospective operational actions. A Controlling NDT additionally can make
operational decisions based on such assessments and drive those decisions forward into actuation on the physical twin.
ETSI
ETSI GR ZSM 015 V
1.1.1 (2024
-
02)
10
Achieving highly accurate behavioural predictions requires that behavioural models have access to as much current data
as possible, representing in detail the "twinned" physical network, services, traffic, environment etc. The use by NDTs
of copious and current data specific to the physical networks they represent lies at the heart of the notion of "twinning"
and distinguishes NDTs from generic behavioural simulations and their uses. However, in many cases, NDTs are used
to predict behaviours that would occur in scenarios - circumstances, actions, etc. - that are at least partly hypothetical or
prospective, rather than strictly representing the actual state of the physical network. In such cases, current network data
may be modified or complemented for use by the NDT in order to specify scenarios for which behavioural prediction is
sought.
4.1.2 Examples of NDT Taxonomy
There are many diverse network and service management automation use cases such as visualization, monitoring,
planning, validation, analytics and optimization, etc. which pose diverse requirements to network digital twins and to
their implementation. To be able to define and describe network digital twins, a common taxonomy would be useful.
The following gives a list of examples of NDT properties and options for each property, which may be used to describe
a network digital twin in the taxonomy or scope:
• Use case: planning, monitoring, optimization, visualization.
• Interaction with the physical twin:
- Including if there is interaction from the NDT to the network, i.e. Analyzing or Controlling, frequency,
characteristics of such interaction, etc.
• Aggregation level: network element, single domain, multi-domain.
• NDT deployment level: application, service management, network management.
• Twinned network size.
• NDT can be used to implement use cases, capabilities, functionalities, and roles that may be mapped to
specific planes such as U/C/M plane.
Below are some examples for plane specific NDTs:
• NDTs may support C-Plane related use cases which controls parts of the network. For example, an NDT for a
C-Plane may simulate various future or expected user mobility patterns and demand distributions (e.g.
coverage or capacity or service distributions) modelling of future events, generate relevant policies for the
network and provisioning them to the PCF. The power of NDT in these cases specifically is its ability to
accurately evaluate the real network's response to future or predicted demands as well as the network's
behaviour. The best outputs of the NDT are then ready for ingestion to the network.
• NDTs may support U-Plane use cases such as estimating the impact of potential UPF QoS policies on the
current traffic pattern. Such use cases need access to the real traffic or matching traffic patterns rather than
working with a statistically simulated traffic mix.
• NDTs may support M-plane use cases by providing emulation or simulation of management functionality such
as configuration management, performance management fault management, services and processes of the
management plane of the physical twin.
4.2 Generic benefits of Network Digital Twin
The following benefits can be obtained from network digital twins:
• A network digital twin may have access to real-time data, which facilitates accurate verification of network
and service configurations, deployments, etc., before their application on the counterpart physical network.
This reduces operational risks and unintended adverse impacts.
• A network digital twin may have access to historical as well as current data, so that it can "replay" a historical
status, for example to analyse past network and services issues (e. g. failures, network congestions, etc.). In
addition, data analysis can be used to predict potential network and service issues in the future.
ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
11
• A network digital twin may have access to additional contextual data (e.g. environmental data, etc.), which
allows verification, simulation, etc. in a realistic environment.
• Network digital twins facilitate data sharing and organizational collaboration. For example, in the case of a
natural disaster forecast, the autonomous network can be informed of potential issues and it can make
automatic adjustments based on this.
NOTE: Additional advantages that fit in terms of network digital twin is for further study.
4.3 Emulation, Simulation and Modelling Time
An NDT is a digital replica of its corresponding physical twin. The fidelity of the correspondence is generally of
primary concern. Such fidelity is determined by two factors:
a) The completeness, accuracy and currency in time of physical twin-related data available to the NDT. Such data
is used by models that represent network, element, service or related states, configurations or conditions (e.g.
YANG models), and by functional or behavioural models that emulate or simulate behaviours.
b) The completeness of state models describing states, configurations or conditions, and the quality of functional
or behavioural models that emulate or simulate behaviours.
Functional or behavioural models may represent either emulations or simulations. In a computing science context,
emulation typically refers to the complete imitation of a machine running binary code. The objective of this is to
duplicate as exactly as possible the detailed processes by which the emulated object operates, which is a satisfactory
general description of emulation methods. Simulation, on the other hand, makes use of mathematical models,
algorithms, transfer functions, etc. in order to generate targeted behavioural predictions. An emulation mimics in detail
the detailed workings of an object and thus may capture a broad range of its detailed behaviours; a simulation operates
at a more abstracted level and focuses more narrowly on particular aspects of behaviour.
As an example, consider the examination of traffic-dependent congestion on a network. An emulation approach might
model traffic as actual series of frames, which are buffered to varying degrees - leading to delays and frame discards - at
individual elements across the network. Metrics of interest, such as frame loss and delay statistics, might then be
determined from inspection of the outcomes of this detailed modeling. A simulation approach, on the other hand, might
use statistical models to estimate these metrics directly.
The use of emulation or simulation may be required or preferred depending on circumstances. For example, physical
behaviours, such as thermal generation, noise generation, wave propagation, etc. cannot be emulated by a digital
replica. NDTs should use simulation methods to predict such behaviours. On the other hand, some behaviours that
derive from digital functions and operations might best be predicted by emulation methods. Still other behaviours might
be adequately predicted by emulation or simulation. Finally, hybrid techniques may be envisaged, wherein particular
behaviours are modeled on atomic elements using simulation methods, while network-level behaviours are determined
by assembling the results of such "micro-simulations" on an emulation-like basis. The types of behaviours to be
predicted, for what purpose, and with what needed fidelity or precision, thus determine not only the use of emulation or
simulation methods, but also influence specific choices regarding model types, construction and execution.
Requirements on what might be called "modelling time" may also influence or be affected by choices regarding
modelling methods. As emulation replicates physical twin operations and processes in detail, it should to a large degree
respect sequences and relative timing of operations, processes and their consequences. Emulation therefore is time-
based, with timing coordination required between the physical and digital twins. Retrospective, forward-looking and
accelerated emulation of events are not precluded, given appropriate timing coordination management; however,
forward-looking or accelerated emulation may involve considerable demands on NDT computing resources, as
operations and events should be "played out." Simulation is typically less rigorously time-based. In some circumstances
it may involve no notion of time whatsoever: e.g. given a particular, postulated hypothetical state and conditions,
predict other aspects of the same hypothetical state and conditions. In general, simulation may permit a full or partial
"collapsing" of time and events. In some circumstances this can lead to a relative greater efficiency, in computational
resources and execution time, of simulation vs. emulation.

ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
12
4.4 Industry progress of Digital Twin
4.4.1 Introduction
The process of standardization of the Digital Twin started several years ago mainly driven by the industry 4.0 and the
need to standardize the architecture for the digital representation of processes for smart factories. Within this push, the
ISO established the Digital twin framework for manufacturing (ISO 23247 series of standards [i.14]).
However, only lately ICT related Standards Developing Organization (SDO) have started the process of standardization
of a network digital twin.
4.4.2 Digital Twin Industrial progress
With the increase in digitalization, adaptation of the digital twin technology in various industries and fields have been
increasing too. This clause summarizes some of digital twin related industrial activities in the non-telecom domains.
The standardization efforts in ISO are paying more attention to digital twins in industry and relative fields.
Committee 184, and its subcommittee "Industrial Data" has a standard series for smart manufacturing, and several other
digital twin standardization projects related to industrial data and systems. ISO also created a work group named
ISO/IEC JTC 1/SC 41/WG6 which specifically focuses on digital twin standardization, including concepts, terminology
(ISO. ISO/IEC AWI 30173 [i.23]), use cases (ISO. ISO/IEC AWI 30172 [i.22]) and related technologies of digital twin
(ISO. ISO 23247 (2021) [i.14]).
The International Electrotechnical Commission (IEC) has a digital twin related working group IEC/TC65/WG24 which
provides guidance for Asset Administration Shell (AAS), which can be considered as an implementation method of
digital twin in smart manufacturing. AAS provides solutions for real world asset representation in the information world
by structures, properties, and services in order to benefit industrial operation and management process (IEC.
IEC 62832-2 (2020) [i.15]).
The IEEE-SA Digital Representation Working Group (IEEE-SA DR_WG) provides a series of standards in digital
representation for various elements in the digital twin. IEEE 1451 [i.16] proposes a solution for sensor interface, it
provides a common interface by creating a self-descriptive electric datasheet and a network-independent smart
transducer object model, which allows sensor manufacturers to support multiple networks and protocols, thus
facilitating the plug and play of sensors to networks:
• Standard series IEEE 2888 [i.17], this standard series comprehensively defines interface between cyber (digital
twin) and physical world.
• IEEE P2888.1 [i.18] and IEEE P2888.2 [i.19] defines the vocabulary, requirements, metrics, data formats, and
APIs for acquiring information from sensors and commanding actuators, providing the definition of interfaces
between the cyber world and physical world.
• IEEE P2806.1 [i.20] proposes digital representation for digital twin, it defines high-speed protocol conversion,
unified data modelling, and data access interfaces for heterogeneous data situations in the digital twin.
• IEEE 2888.3 [i.21] provides a framework overlooking interactions between general objects in cyber and
physical world, including capabilities to interact between physical things and digital things (cyber things),
capabilities to easily integrate with backend infrastructure / integrate with other external systems, capabilities
to access to things by authorized parties, capabilities to describe physical devices, virtual devices, or anything
that can be modelled.
The Digital Twin Consortium is a worldwide industry association that aims to boost the growth and use of digital twin
technology. By bringing together top companies, academic institutions, and government organizations, the consortium
seeks to foster collaboration and promote the progress of digital twin technology across a wide range of industries such
as healthcare, aerospace, and manufacturing (with over 200 organizations involved). Their goal is to encourage the
widespread adoption of digital twin technology, create new business opportunities, enhance efficiency, and drive
innovation. Additionally, the consortium is actively engaged in the development of digital twin technology standards,
including the ISO 23247 [i.14] standard for digital twin framework and the IEEE 1451 [i.16] standard for digital twin
data interoperability.
ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
13
4.4.3 Standardization of the Network Digital Twin
ITU has published the Recommendation ITU-T Y.3090 [i.7] which describes the requirements and architecture of a
Digital Twin Network (DTN) as defined in the ITU-T. At this time, version 1.0, published in February 2022, is
enforced. The scope of the recommendation includes:
• Functional requirements of DTN
• Service requirements of DTN
• Architecture of DTN
• Security considerations of DTN
IRTF has done the most extensive work on NDT so far with several internet-drafts published. The main draft [i.3]
provides the concept, basic definition and reference architecture for the NDT.
Within IRTF, there are also a number of interesting individual drafts (at the time of writing not yet endorsed by the
IRTF). These include:
• Requirements for Interfaces of Network Digital Twin [i.8]: which defines requirements for interfaces for the
Network Digital Twin, including northbound interfaces to applications to use the capabilities provided by the
NDT, southbound interfaces between the digital twin and its physical counterpart, and internal interfaces.
• Accurate prediction of packet network performance metrics [i.9]: an NDT that predicts metrics such as end to
end path/link delay, jitter, and loss for a packet network; optical channel terminal powers and margins for an
optical network.
• High-precision simulation of network traffic [i.10]: an NDT that simulates traffic flows by replicating the
forwarding paths, network metrics and key characteristics (e.g. flow rate, five-tuple information, data packet
length, and data packet priority) of the real network traffic flows.
• Accurate measurement of network delays [i.11]: an NDT that can simulate segment-by-segment or end-to-end
packet delay measurements.
China Communications Standards Association (CCSA), technical committee 3 also has a working group working on
the standardization of the NDT. Their progress is currently similar to that of the IETF with the standardization of the
digital twin architecture.
4.4.4 Synergies between Industrial DT and NDT
With industry 4.0 more and more industries and enterprises (e.g. banking, manufacturing, retail, transportation,
hospitals, government, etc.) are embracing digitalization. One of the technologies that aid digitalization and bring in
efficiency is the Digital Twin technology. The DTs from industries include robot DTs, production line DTs, or any
other DTs that are twinning an industrial entity (such as a cloud-controlled robot). Refer to clause 4.4.2. for Digital
Twin Industrial progress. Communication networks provide the mission critical communication services to the DTs
from industries and enterprises. NDT plays a key role in providing such communication services. NDTs may
collaborate with DTs from industries and enterprises. The scope of the collaboration may be mutual adaptation and
interworking between the NDT and DT. Such collaboration may include:
• The network may adapt its telecommunication service to the requirements of the DTs. Adaptation of
communication services to the exact requirements is critical in case the requirements include determinism,
such as time sensitivity, high reliability, and predictability (that is, dependability on the fulfilment of service
requirements not only momentarily but during the lifetime of critical workflows or operations). Determinism is
a requirement that is present in industrial private networks, but it is also relevant in other areas such as
distributed real-time audio/video production requiring high synchronicity or group communication between
physical entities coordinating a collaborative task (e.g. robots moving in 2D or 3D). In order to adapt the
communication services to the exact needs of these use cases, especially in a predictable manner, the network
may use its NDTs to carry out the necessary (predictive) analytics and decision process that yields the
(re-)configuration of network resources and services via the network and service management services.

ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
14
• The DTs may also adapt their behaviour to the capabilities of the network, e.g. by selecting a synchronization
frequency or a physical motion speed that can be safely maintained through the level or service provided by
the network.
• Collaboration between NDT and DTs may also be for solving an end-to-end industrial process automation task
that has complex responsibilities distributed across industrial devices and their controllers, the communication
network (i.e. to provide communication and mobility services), and other business solution components that
are outside of the communication network's or its NDT's reach.
• Integration of NDT and DT may also enable management of communication network as part of a vertical
system, like a production system of the vertical industries.
The collaborations described above may be studied as part of future work.
5 Examples of use cases using NDT
5.1 Radio network energy saving
5.1.1 Description
The objective of energy saving is to lower OPEX for mobile operators, through the reduction of power consumption in
the mobile networks that is becoming more urgent and challenging. One typical scenario of energy saving is to reduce (or
switch-off) radio resources when the traffic demand is low, and re-activate them on a need basis. But, the energy saving
actions may deteriorate the service experience (e.g. throughput, coverage, etc.), and it is not straightforward to evaluate
the influence on service experience of energy saving actions beforehand. NDT provides a further way for verification of
energy saving actions.
5.1.2 Use case details
This clause describes the detailed steps that the NDT may be used for the intent-based closed loop:
1) When receiving an intent related to radio network energy saving from an Intent Owner, the Intent Management
Function translates the intent and derives the energy saving actions to satisfy the intent.
2) The Intent Management Function applies these derived actions on the NDT for verification. Typically,
examples of these actions include "switch on some energy saving algorithms in the cell", "configure the cell
overlaid relations" etc. By performing these actions, the NDT sends the relevant performance metrics (e.g.
energy consumption, throughput, weak coverage ratio, and maximum UE number) to Intent Management
Function for evaluation.
The interactions between Intent Management Function and NDT may be performed multiple times to compare among
different sets/configurations of energy saving actions. Following the default behaviour of an intent-based system, the
intent-based system will perform the closed-loop automation to satisfy the intent.
5.2 Network Slicing risk prediction
5.2.1 Description
As described in clause 7.1 of ETSI GS ZSM 003 [i.5] the required SLA for a network slice is translated into a set of
service profile parameters which in turn are further translated into configurable parameters or intent expectations for the
network slice profiles of each MD (normally CN domain, AN domain and TN domain). Using the NDT to predict risks,
the ZSM framework can identify risks of specific service or network slice profile parameters not being met due to
changing traffic and network conditions (e.g. a MD not being able to provide the network slice latency it committed for)
and the NDT supports the ZSM framework to take actions before these risks materialize and therefore before the
committed SLA/SLS are broken.
ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
15
5.2.2 Use case details
A precondition of this use case is that the network slice is established and running in the network.
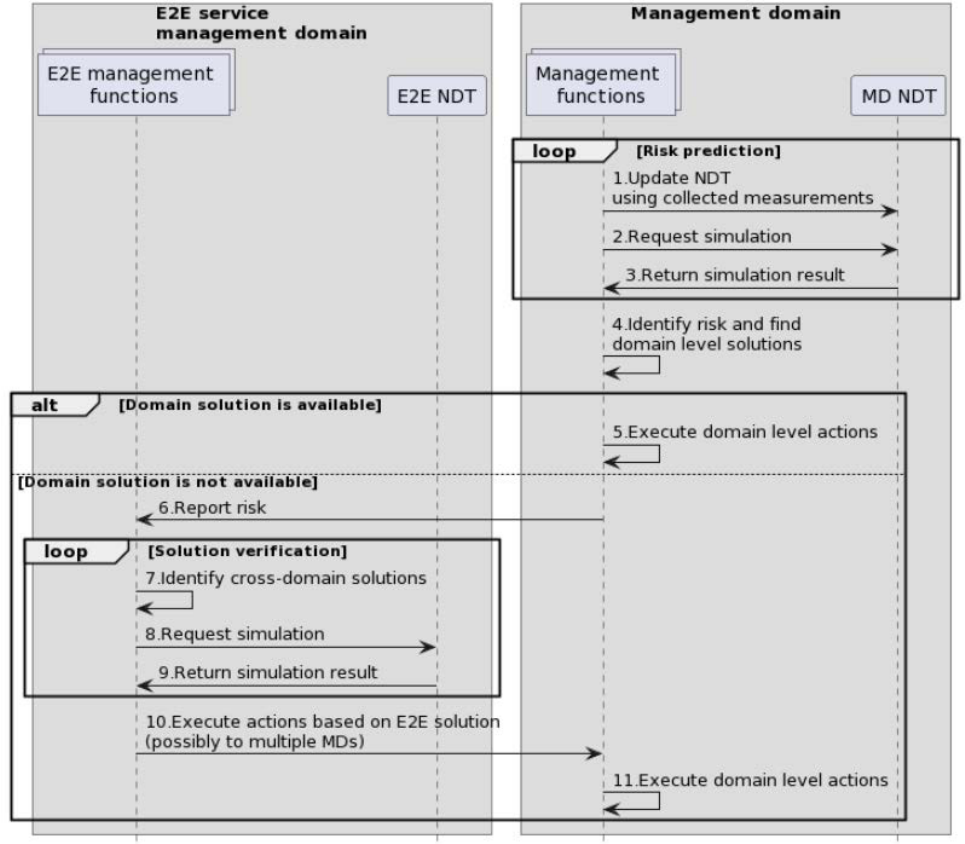
This clause describes the sequence how the NDT may be used for the prediction of risks in network slicing:
1) Steps 1 to 3 of figure 5.2.2-1: Measurements collected from the physical twin are constantly used by the NDT
to perform simulations and to identify possible risks for network slice parameters to be outside of the expected
range for these parameters in the near future.
2) Steps 4 to 6 of figure 5.2.2-1: When the prediction results indicate that the simulated parameters will be
outside of the expected ranges it will attempt to identify a solution for the risk. If it can find a solution to avoid
the risk within the MD, it will implement it by executing domain level actions. If it cannot find a solution it
will report the risk to the subscribed MnF(s) in the E2E SMD using a domain analytics service as described in
clause 6.5.3.2.1 of ETSI GS ZSM 002 [i.6].
3) Steps 7 to 9 of figure 5.2.2-1: Using the risks information reported by the prediction service, as well as other
performance measurements collected from the different MDs, the E2E SMD MnF will request one or multiple
simulations from the E2E NDT in order to identify a valid solution that would avoid the risk for materializing
and the SLA/SLS of the network slice being broken.
4) Steps 10 to 11 of figure 5.2.2-1: Once the E2E SMD MnF identifies the valid solution it will communicate it to
the appropriate MD MnFs using a domain orchestration service as described in clause 6.5.5.2.1 of ETSI
GS ZSM 002 [i.6].
ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
16
Figure 5.2.2-1: Example of simplified sequence diagram of network slice risk prediction and healing
5.3 Signalling storm simulation and analysis
5.3.1 Description
During mobile network service disruption, terminal users will repeatedly attempt to establish connections until they are
reconnected. The explosion in the volume of reconnect signals in such scenarios might overload network processing
capacity in the core network. This might in turn lead to a signalling storm, eventually causing serious impacts on
network performance.
5.3.2 Use case details
The adoption of the NDT can predict the amount of signalling traffic based on the number of users, and to analyse the
impact of optimization actions derived by management services (e.g. domain intelligence services). While handling
signalling traffic, the network digital twin provides the capabilities as described below:
1) The NDT could predict terminal reconnection growth in the physical network. To do so, it could utilize data
such as the number of current subscribers, signalling traffic collected in recent and historical periods, predicted
or estimated recovery durations, and any other relevant data to predict maximum terminal reconnection
growth. This predicted information may be consumed by management services (e.g. a proactive network
optimization service as defined in clause 6.5.3.2.1 of ETSI GS ZSM 002 [i.6]) for optimization analysis.
ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
17
2) Based on the predicted maximum terminal reconnection growth, optimization (e.g. set the maximum rate of
traffic received at a network node) is triggered, and the NDT can be used to validate the impact of the
optimization actions.
5.4 Machine Learning Training
5.4.1 Description
In order to utilize Machine Learning (ML) model, the model used for ML should be pre-trained. In a common approach,
ML models are typically trained in the following way [i.3]:
1) Train an ML model using imported data in a specific training environment (e.g. the ML developer lab).
2) Retrain an ML model with data measured in the context of a deployed environment when deploying the model
to a deployed environment.
The traditional method involves training in multiple stages, which consumes human resources and time to build the
environment and measured data. By using the NDT, however, it is possible to acquire data from the NDT automatically,
which reflects the situation of the deployed environment in real time for model training resulting in cost reduction as a
benefit.
Furthermore, clause A.3 in ETSI GS ZSM 012 [i.13] describes the need for performance evaluation of the ML model
post-deployment after deployment to a deployed environment. Therefore, the performance can be evaluated using a
sandbox environment. By using NDT it is possible to evaluate the performance of an ML model in a realistic virtual
environment provided by NDT before deploying it.
5.4.2 Use case details
Training of the ML model using NDT involves the following steps:
1) The E2E and/or domain management services are instructed to train and deploy the ML model (e.g.
requirements such as accuracy of the ML model or SLAs monitored by the ML model may be given as intent).
2) Training data for the ML model is collected from the real-time data and any other relevant data accumulated in
the E2E service management domain and/or management domain. The AI training data management service
specified in ETSI GS ZSM 002 [i.6] can be used to measure the data.
3) E2E and/or domain management services use the data acquired in Step 2) to train the ML model. After the
training is completed, the deployed AI model performance evaluation service and deployed AI model
assessment service specified in ETSI GS ZSM 002 [i.6] are used to evaluate the ML model to see if they meet
the requirements given in Step 1).
4) Upon completing the training after acknowledging the ML model meets the requirements, the ML model is
deployed. If the requirements are not met, return to Step 3) to retrain.
5.5 DevOps-Oriented Certification
5.5.1 Description
CI-CD-based management operations such as upgrade may be used for software introduction or update on physical or
virtualized network (e.g. newly establishment or version upgrade of software).
By incorporating verification using NDT into the CI-CD process, it is possible to have a verification in NDT which is
similar to the deployed environment to support service assurance and SLA. In addition, the verification can be
performed automatically in the CI-CD process without human intervention, leading to zero touch operation.
ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
18
5.5.2 Use case details
Verification using NDT in the CI-CD process can be carried out by the following procedure:
1) The CI-CD process is performed when introducing or updating software. Management services in (E2E)
management domain receive the request of verification in NDT in the CI-CD process, (e.g. requirements to be
confirmed in the verification will be input) .
2) Management services perform verification in NDT to confirm whether the introducing or updating software is
proper and obtain verification results, e.g. request on introducing or updating to the latest version will be the
input or trigger of the intent, the result (e.g. success or failed) will be the output and then use cases may be
used as input of NDT to verify if the software can fulfil the expectation.
3) Management services may return verification results to ZSM framework consumers (e.g. Operators).
5.6 ML inference-impact emulation
5.6.1 Description
ETSI GS ZSM 012 [i.13], clause A.3 describes the scenarios and needs for AI/ML model validation during pre-
deployment / post-deployment and model reality monitoring. ETSI GS ZSM 012 [i.13], clause 4.2 describes the
diversity in the development, deployment environments and various types of trainings. ETSI GS ZSM 012 [i.13],
clauses 4.2.3.1 and 4.2.3.2 describe the ML model validation service and ML sandbox configuration service
respectively. An ML Entity can be an ML model or ML enabled service which may be used in one or more network and
service management use cases.
As described in ETSI GS ZSM 012 [i.13], clauses A.3 and 4.2 after an ML Model is trained, validation is done to
ensure the training process is completed successfully. The validation of an ML model is done to check whether the ML
model has achieved the required accuracy. After the training and the validation of the ML model accuracy, the ML
Entity may need to be evaluated to confirm its performance in its intended network and service management use case.
For the MnS consumer (e.g. operator) to validate the ML Entity's performance, it may be necessary to apply the
decisions of the ML Entity in a sandbox environment. The sandbox environment may be the twin of the relevant parts
of the network and its environment. The ML Entity decision may include recommendations or proposals for changes to
the network. The network and its management system need to have the capabilities and provide the services needed to
enable the consumer to request inference action impact evaluation of the ML Entity and receive feedback on the
evaluation of a specific part of ML Entity or the application or management function that contains an ML Entity. An
NDT in the ZSM framework may provide sandbox or emulations service. As such, the ML inference emulator use case
may use the ZSM sandbox configuration service (ETSI GS ZSM 012 [i.13], clause 4.2.3.2), with possible extension /
modifications, to achieve the required emulation. Description of possible extension or modifications would be part of
future specifications.
5.6.2 Use case details
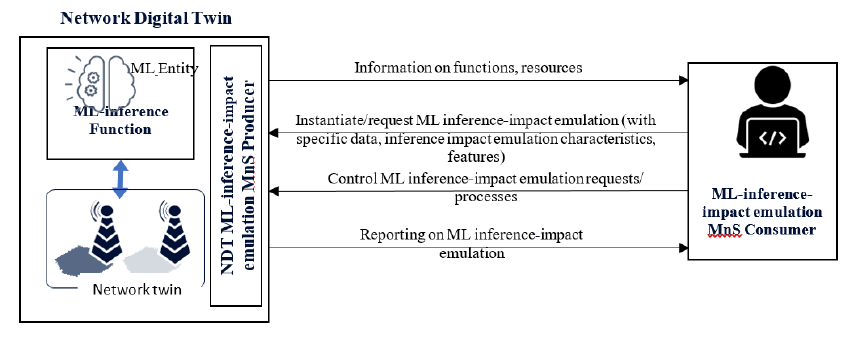
Authorized consumer or MnS such as ML model validation service may wish to request an NDT based sandbox which
has ML Inference-impact Emulator for the execution of ML inference-impact emulation for a specific ML Entity. It is
assumed that the NDT as sandbox gets current network, topology, inventory, configuration, environment related data
and any relevant data to build the emulation environment emulating the real network. Accordingly, an NDT in the ZSM
framework as a sandbox or the producer of ML inference emulation MnS may provide the below capabilities:
1) For the NDT as MnS producer to provide information about the ML inference-impact emulator, its features
and operations, e.g. about the characteristics of an ML inference-impact emulator, ML Entities under
execution or the available execution resources. Such information can be used by authorized MnS consumer to
discover or subscribe to available ML Inference impact emulator services and request for the same when
required,
2) For an authorized MnS consumer to request an ML Inference-impact Emulator to execute ML inference-
impact emulation or to create an instance of the ML inference-impact emulation process for a specific ML
Entity.
ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
19
3) For an authorized MnS consumer (e.g. an operator) to manage the ML Inference, e.g. to start, suspend or
restart the inference-impact emulation; or to adjust the inference-impact emulation characteristics such as the
reporting characteristics.
NOTE: The above figure shows potential interactions between the ML inference impact emulation MnS consumer
and producer. This does not represent the sequence of the interaction.
Figure 5.6.2-1: Use, management, and control of the NDT-based
ML inference-impact emulation process
5.7 A QoT-Oriented NDT for Optical Networks
Amplified optical transmission networks may feature transmission bit rates and distances that are limited by noise
accumulation and other impairments. Amplified spontaneous emission noise from optical amplifiers is a key
transmission impairment, and other factors including various nonlinear effects, channel filtering, etc. also contribute to
transmission performance limitations. Additionally, optical amplifiers couple optical power and noise evolutions among
channels, resulting in complex, hard-to-predict behaviours in multi-channel systems.
An NDT relevant to optical network operations computes transmission performance, or Quality of Transmission (QoT),
on provisioned or prospective optical transmission channels, as described in [i.12]. That is, it computes, as and when
requested by applications, the margin that is or would be available at channel end points, margin being the further
received signal to noise ratio degradation that could be tolerated before pre-correction bit errors rise above a critical
threshold. Computation of margin would be in respect of either operating optical channels in the actual network and
service state, or on actual and/or prospective optical channels in some hypothetical, alternative network and/or optical
connection service states.
The QoT information provided by this NDT is described in [i.12] as critical in enabling automation of various
operations:
• Automated margin surveillance on operating channels: e.g. supporting channel degradation prediction with
time-based analysis and forward projection of margin evolution.
• Automation of optical channel provisioning: channel margin evolutions, occurring throughout trial channel
power-up/down batches and sequences, are evaluated on the NDT until a combination is found that preserves
performance integrity on existing and new channels throughout the whole sequence of operations. This
combination can then be pushed directly into actuation.
• Risk mapping: the QoT NDT is used to identify scenario-based optical channel performance risks on operating
and new optical channels. Scenarios of interest include prospective fibre and equipment failures, restoration
actions, add/drop/reroute, etc.
ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
20
• Dynamic restoration optimization: risk mapping on planned optical channel restoration configurations may be
used, when post-restoration performance risks are identified, to trigger determination of new restoration maps,
whose performance integrity is assured by use of QoT-NDT. Where such new maps are pushed directly into
active status, full closed loop operational automation of assured-performance dynamic restoration planning is
achieved.
• Brown-field network planning: QoT-NDT is used in support of optimization of new equipment additions and
optical service configurations. Accurate transmission performance prediction not only assures the operational
integrity of services on the planned network, but reduces requirements for "spare" margin allocations,
enhancing the overall resource efficiency of the optical network.
As described in [i.12], key static models used in optical QoT-NDTs relate to optical network and service topology
specification. Key behavioural or functional models relate to the determination of margin impacts resulting from the
various QoT impairments, including amplifier noise, nonlinear propagation effects, and filter shaping of channel
spectra. Such functional models are representable as transform functions: e.g. given a set of channel powers at the input
to an amplified, channels powers and signal-to-noise ratios are generated. Data from the network, used to "feed" the
models for QoT prediction, relates mainly to channel power and spectral measurements, although more "advanced"
measured data like linear and nonlinear SNRs, channel centre wavelength excursions, etc. may - if available - improve
prediction results by reducing the extent and complexity of functional or behavioural modeling required to estimate
transmission performance.
5.8 Network Playback to perform historical incident analysis
5.8.1 Description
Communications network playback refers to the ability to analyse and understand the historical status and behaviour of
a network over time in order to avoid the incident from happening in the future or to minimize the effects of future
incidents. Network playback capabilities offered by an NDT could include the following:
• Historical data inspection: enables to gain visibility into the performance, availability, and reliability of the
communications network in the past. This could help in the identification of patterns, trends, and anomalies
that can lead to network issues.
• Troubleshooting of historical network events and incidents: replays the historical data, supports the analysis of
the sequence of events leading up to a particular issue or network outage, helping operators identify the root
cause.
• Historical what-if analysis: supports the exploration of different scenarios and assesses the outcomes if certain
changes or decisions had been made at the time. It involves leveraging historical data to simulate alternative
courses of action and evaluate their potential impact in the communications network.
5.8.2 Use case details
An authorized ZSM consumer or MnS may wish to perform a post-mortem analysis on a historical event and simulate
what different courses of actions could have been taken. An NDT in the ZSM framework may provide the following
capabilities:
1) The NDT as an MnS producer to provide historical data to an authorized ZSM consumer based on the time of
the historical event to be analysed as well as the duration of the analysis (time before and after the event to be
analysed).
2) The NDT as an MnS producer to provide the replay of the historical data as it happened.
NOTE: Replay of the historical data refers to the reproduction of the conditions and events that occurred during
the chosen historical period.
3) The NDT as an MnS producer to provide what-if capabilities using historical data together with modified data
(for example modified configuration parameters on the historical data) and predicts the effects of these
changes in the network.
ETSI
ETSI GR ZSM 015
V1.1.1 (2024
-
02)
21
5.9 Data generation for NDT
5.9.1 Description
In some cases, the collected data for the network digital twin is not sufficient on the quality and/or quantity, and
therefore some additional data may be needed. A possible mechanism for obtaining the additional data may be synthetic
data generation such as data interpolation, data extrapolation, data inference, data generated by another NDT, etc. Then
the synthetic data can be used for the network digital twin, such as creating or updating digital twin models.
NOTE: The measurement of the quality (such as accuracy) of the data related to NDT and how to validate it is for
further study.
5.9.2 Use case details
In this use case, the synthetic data generator enables to manage synthetic data that is required to create or update digital
twin models (e.g. service models, behavioural models, etc.). Generally, the synthetic data generator may be part of the
NDT. Additionally, an NDT can have the capability to provide synthetic data for another NDT in some scenarios. For
example, the synthetic data from one NDT can be used as the input of another NDT.
As a prerequisite, the synthetic data generator used for the NDT is deployed and available in the ZSM framework.
Following steps show an example of the NDT workflow with synthetic data generator:
1) Based on the requirements of specific use case, the collected data obtained can be provided to the NDT.
NOTE: This step is for required data that can be obtained by configuring the collection frequency, collection
method, storage, etc.
2) NDT MnS producer can ascertain whether the data is sufficient, and then trigger the synthetic data generator to
generate synthetic data for the current NDT solution if required.
3) NDT MnS producer will validate the synthetic data in different approaches (e.g. comparing to the real data),
and then the synthetic data generator producer may trigger subsequent optimizations accordingly. For
example, optimize the algorithm (e.g. interpolation algorithm) or model (e.g. GAN) for synthetic data
generation with the up-to-date collected data if the accuracy of the synthetic data is degraded.
5.10 NDT resource management and orchestration
5.10.1 Description
Network digital twins are expected to enable a wide range of use cases as described in clause 4. The use cases may call
for different information, models, and use case specific descriptions. Either the same consumer or different consumers
may request more than one similar NDT-MnS that are inherently connected (e.g. serving same region or providing
similar NDT MnS for visualization or what-if analysis services etc.). Although each request may potentially invoke
different capabilities of NDT, which may be realized by different means, it may be that all or part of the underlying
data, models and capabilities of these requests may be similar. An NDT in the ZSM framework may have the capability
to facilitate concurrent request processing, to share NDT capabilities efficiently and independently, instead of
sequentially, while taking into account the service timeframe so as to improve the resource utilization and, thus, gain
efficiency e.g. energy efficiency.
NOTE: Impacts, if any, by resource shared controlling NDT MnS is for further study.
This brings a need to support the NDT resource management and orchestration service that provides services and
capabilities for efficient resource utilization. This service also improves the visibility into the requests belonging to the
same network and provides effective resource utilization. The following scenarios could be envisioned for NDT
resource management and orchestration service MnS:
• When a new NDT- MnS is requested, the NDT MnS producer will decide if a new instance of the service is
needed:
- if no similar services are running;
ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
22
- if the NDT MnS does not support concurrency and resource sharing.
• When a new NDT MnS is requested, there may be similar services running and if the NDT MnS has the
capability to support concurrent existence or resource sharing capability, then the NDT MnS producer may
decide to reuse existing instance either by fully or partially sharing the resources.
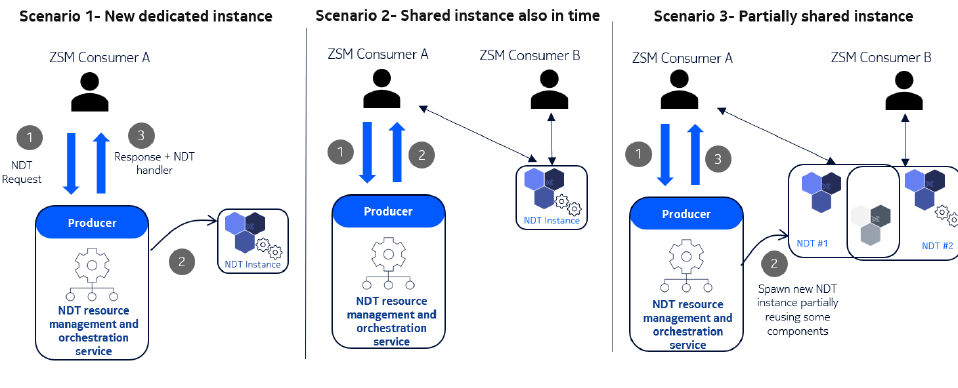
A consumer can place an NDT MnS request for a use case or a particular configuration of a use case and be assigned a
dedicated instance as can be seen in scenario 1 in figure 5.10.1-1. In scenario 2 in figure 5.10.1-1, two or more
consumers could be asking for a common sharable capability such as monitoring of a particular network, in which case,
the consumers can be assigned a fully shared instance. An example for fully shared instances is the real-time monitoring
of traffic or other related KPIs in different granularity.
As seen in scenario 3 in figure 5.10.1-1, two or more consumers requesting for similar NDT MnS may use models or
information from the NDT MnS capabilities partially such that no conflicts and adversarial impacts may occur or be
observed. For example, in partially sharing of the instances, 2 NDT instances performing different predictions in the
RAN network can share the environment component as they would need information about the same environment.
These two instances share the same environment, yet they have their own RAN digital component.
Figure 5.10.1-1: NDT resource management and orchestration service scenarios
In addition, resource sharing makes management of syncs of the NDT to the physical network twin easier. The resource
management and orchestration service in NDT facilitates the allocation of resources to requests in such a way to avoid
inefficient allocation of resources, negative impact over the mobile network operations (load generated to create and
maintain NDTs synched), and energy efficiency, but more importantly it provides the possibility of correlating
information and knowledge beyond a use-case or consumer group.
5.10.2 Use case details
In the above context, if there are NDT MnS which support concurrency and resource sharing in ZSM framework then
an NDT resource management and orchestration service enables the concurrent processing of the service requests by
grouping consumers, granting authorization, sharing of the resources and thus, effective utilization of NDT MnS.
Below are potential capabilities related to NDT resource management and orchestration service:
1) Determine whether a new NDT MnS instance is needed or existing instance could be used by utilizing the
discovery service and information about NDT MnS that are currently being provided.
2) Ensuring the needed isolation required for simultaneous existence of several service requests by any of the
following means:
a) Creating a new dedicated instance.
b) Allocating subsequent request(s) to a partially shared instance comprising of parts of an existing instance
based on resources, conditions, and possibilities.
ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
23
c) Allocating subsequent request(s) to fully shared instances either in time-shared mode or capability-
shared mode or both. In case of time-shared mode, it may be that only the functional or behavioural
model is shared. Example of capability shared are visualization, what-if-analysis etc.
3) NDT resource management and orchestration services informs the authorized MnS consumer about the
acceptance of the request and details of the MnS producer instance.
4) NDT resource management and orchestration services may trigger deletion of instances that are no longer
required.
5) Providing report on NDT resource utilization upon request by an authorized consumer.
5.11 NDT Time Management
5.11.1 Description
This clause addresses two aspects related to Network Digital Twin time management.
A Network Digital Twin synchronizes its state with the physical twin. The synchronization of the NDT state with the
physical twin state is not instantaneous. Each time frame in an NDT time sequence corresponds to a point in time in the
physical twin as shown in figure 5.11.1-1. For example, if the physical twin state is x at time t then for NDT to replicate
the state x the time would be t plus some time delay. So, there will always be a time delay, say NDT time delay, which
is when physical twin state is replicated in the NDT. For example, delay critical NDT applications may prefer to
minimize it by various means. Additionally, when the NDT performs simulation for answering what-if questions, its
time synchronization may be lost, for example if the simulation is paused. In such case, NDT may require
re-synchronization with the physical twin time. These scenarios bring the need for the NDT virtual time to be
synchronized with the physical twin time.
Figure 5.11.1-1: NDT time delay
The NDT virtual clock manages NDT virtual time in NDT MnS and has capability to start, pause etc. The NDT virtual
time may be future time or past time (e.g. playback use case described in clause 5.8), whether the simulation needs to be
accelerated or decelerated, etc. There may be additional capabilities for the NDT virtual clock which is for future study.
Physical Net work Time
NDT Time
NDT Time Delay
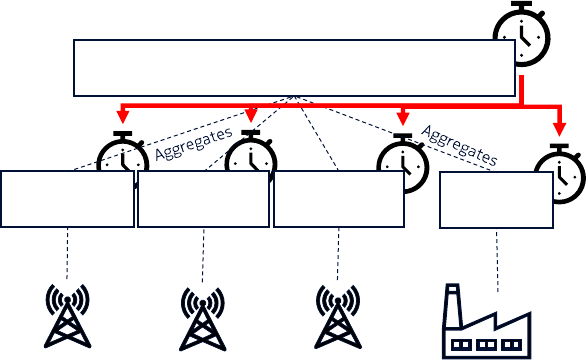
ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
24
Figure 5.11.1-2: An example of synchronization of NDT components to the NDT master virtual clock
Considering an example, network-level NDT, as show in figure 5.11.1-2 which needs to interact with network element
level NDTs or with environment DTs that have their own models, there is a need for being able to synchronize time
between these. For example, if an NDT is used to simulate the impact of configuration changes for network slicing
proposed by network automation functions, the NDT simulation may be initiated to a specified network state at a
specified time. It may also be required to change the simulation related time configuration, for example to simulate a
future point in time. The simulation may require several simulation elements, like NDT simulation models for different
network elements, slices, or for the network environment to interact and they may be provided by more than one
vendor. For this reason, when simulating a specific point in time or an event, the different simulation elements may
need to be synchronized in time:
• The NDT virtual clock at the network-level NDT in the example above may play the role of NDT master
virtual clock to which these interworking digital twins may need to time synchronize.
• The NDT virtual clock may be provided by the NDT or by a separate service.
• The need to configure and monitor time or utilize NDT virtual clock depends on the use case and the
modelling method employed.
Further time management related concepts and NDT time management services are for further study.
5.12 NDT consumer preference
5.12.1 Description
ETSI GS ZSM 002 [i.6] clause 6.3.2. describes the registration service and discovery service. An NDT MnS producer
uses the registration service to publish its capabilities. The discovery services enable the authorized MnS consumer to
discover the NDT MnS capabilities.
An NDT MnS, depending upon the network or service management use case, might need data originating from various
sources (network data, environment data, analytics, UEs data, etc. described in clause 4.1) and suitable
hardware/software resources to function properly. MnS consumers would prefer to specify needed NDT characteristics
or configurations to the NDT MnS producer tailored to fulfil consumer specific needs i.e. to define the consumer
preference for the specific NDT MnS. For example, consumer preferences may be related to environment data sources
e.g. weather, synthetic data etc, data characteristics (e.g. robustness, data granularity, maximum tolerable latency) sync
characteristics (such as sync pattern, triggers, frequency, duration, criteria, etc.), required NDT output latency,
characteristics of the service to be twinned, resource constraints (HW/SW) etc. Furthermore, in the case that consumer's
preference on NDT MnS characteristics or configuration may change over time and MnS consumer may update the
NDT MnS producer with the needed changes. ETSI GS ZSM 002 [i.6], clause 6.3.2.5 describes Management capability
exposure configuration service. Consumer preference for an NDT MnS may be specified as optional or specialized or
enhanced service or capability to this ETSI GS ZSM 002 [i.6] service.
Network-Level NDT
NE-1
En v i r on m e nt
NE-1 NDT
NE-2
NE-3
NE-2 NDT NE-3 NDT
En v DT
NDT Mast er Virt ual Clock
Models
Models Models
Models
NDT Virt ual Clock
Synchronize
ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
25
5.12.2 Use case details
Below are the steps involved for the authorized consumer to specify its preference for the NDT MnS:
1) An NDT MnS producer registers the services it provides and its capabilities using registration service.
2) The MnS consumer discovers available NDT MnS through the discovery service.
3) The authorized MnS consumer when requesting an NDT MnS to an NDT MnS producer specifies its
preferences related to the NDT MnS configuration or characteristics.
4) The NDT MnS producer based on the consumer preference may perform feasibility checks. Based on
feasibility to fulfil the consumer preferences the NDT MnS producer may either acknowledge the request or
provide recommendations on potential consumer preference that could be fulfilled.
5) The NDT MnS producer once the customer preference is fulfilled would report about the fulfilment to the
authorized consumers.
5.13 NDT Fault Injection Analysis
5.13.1 Description
Automated diagnosis of network faults is an important and challenging part of self-healing solutions. Diagnosis may be
based, for example, on detected anomaly events and their signature. Anomalies are, by definition, rare, so building a
comprehensive diagnosis knowledgebase is often time-consuming. Fault injection is a way to learn network anomaly
patterns of different faults. Injection of faults is not possible in operational networks as it may hinder normal operation
of the network. Network digital twins offer a non-disruptive way of doing fault injection studies. ETSI
GS ZSM 002 [i.6], clauses 6.5.3.2.1 and 6.6.3.2.1 describe anomaly detection service and E2E anomaly detection
service respectively. These services may utilize NDT fault injection analysis to proactively detect anomalies in the
network, which can be used to provide self-healing services.
5.13.2 Use case details
NDT fault injection analysis flow is shown in figure 5.13.2-1. For the fault exploration, needed configurations for fault
scenarios are created. Fault exploration may include, for example:
• NDT consumer explicitly configure the NDT with fault scenarios to simulate the faults in the NDT.
• NDT consumer configure the NDT with a policy for generating fault scenarios to simulate the faults in the
NDT. This may include, for example, pre-designed scenarios as well as heuristic exploration.
• NDT consumer may provide the NDT a pre-determined fault signature for the NDT to explore potential fault
scenarios causing the provided fault signature.
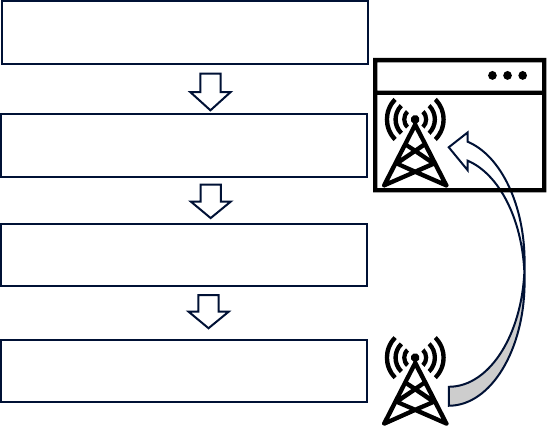
ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
26
Figure 5.13.2-1: NDT-based fault simulation analysis
The fault signature describes the symptoms of the observed faults.
The fault scenario is then simulated in the NDT and the resulting fault signatures are collected. Simulations are never
fully accurate, so it may be necessary to calibrate the fault signatures before providing them to the self-healing MnS.
One method of doing so is to inject known fault scenarios diagnosed in the physical network in the NDT simulation and
compare the simulated fault signatures with the ones observed in the physical network.
The fault signatures and injected fault scenario may be added to the diagnosis knowledgebase of the self-healing or
anomaly detection MnS to determine the root cause and optimize the network.
5.14 NDT data accuracy
5.14.1 Description
As described in clause 4.1. data is an essential part of the NDT, and it can include different information about the
network and its environment, e.g. topology, configuration, performance and fault management data of network elements
etc. The access to the most current data representing in detail the physical twin is fundamental for the performance of
the NDT, e.g. accuracy of the NDT in representing the physical twin. For example, in the case of Analyzing NDT
behavioural predictions, it is crucial that behavioural model of the NDT use the most up-to-date data to represent the
physical twin in order to determine the behavioural impact of changes to the network. However, the NDT may have
access to data of different type, e.g. real-time data or historical data. Therefore, the NDT performance, e.g. accuracy of
the NDT behavioural predictions will be impacted by the type of the data used to represent the physical twin.
5.14.2 Use case details
The Network Digital Twin should behave as accurate representation of the communication network or parts of one.
However, the NDT can be realized using different frequency and latency for network data collection, e.g. historical
data, real-time data, or any combination thereof. Thus, the difference between the NDT and the physical twin that it
represents can largely differentiate based on the data used to realize the NDT, the frequency with which the NDT is
being synced with the real system (as well as the complexity and computational cost of tools used to build the NDT.
Correspondingly, the NDT performance measure depends not only on the properties of the decision logic applied within
NDT, but also on the measure on how accurate the NDT represents the physical twin. This relates to the characteristics
of the data (e.g. real-time, historic nature) used to realize the NDT. Therefore, such measure of data accuracy of the
NDT needs to be determined, monitored and communicated to the authorized NDT MnS consumers. This may include
the following:
• Input data accuracy: Determining the accuracy in input data used in the NDT compared to the physical twin.
Fault explorat ion
Fault injectionsimulation
NDT simulat ion
Calibrat ion
Self-Healing Solution
Physical net work
Fault configurations
Fault signat ures
Fault signat ures

ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
27
NOTE 1: The input data accuracy may be due to difference between the historical data and current data from the
physical twin or NDT data compared with the physical twin at the same time as related to the NDT virtual
time or changes in the physical twin.
• Output data accuracy: Determining the accuracy between the output data of the NDT and the corresponding
behavior observed in the physical twin at the same time as related to the NDT virtual time.
NOTE 2: The output data accuracy may be due to input data accuracy, resource constraints at NDT, performance
issues in the NDT for example due to data drift. It is one aspect of measuring the NDT accuracy.
The knowledge of the performance of the NDT MnS may be utilized to improve the accuracy, if possible, of the MnS
by reconfiguration or if it utilizes AI/ML retraining the ML entity or recalibration of simulations etc. or determine the
scenarios of application of specific NDT MnS.
Based on such determination the following NDT management steps are envisioned:
1) NDT MnS consumer, e.g. operator may request the specific data accuracy to be fulfilled at NDT, for each
input and output data, and monitoring the data accuracy of the NDT. Such request may comprise requirements
in terms of metrics which are to be exposed and conditions under which the metrics will be fulfilled.
2) NDT MnS producer will report the data accuracy based on MnS consumer's requirements.
3) Based on determined data accuracy the NDT MnS producer will determine the need to perform the
synchronization between the NDT and the physical twin. The following cases are envisioned:
a) If the input data accuracy is not meeting the consumer data accuracy requirements the NDT is not using
the most current data, i.e. consumer is expecting more current data to be used by NDT. In such a case the
synchronization from the physical twin towards NDT needs to be performed. The NDT may attempt to
trigger data collection from the physical twin and update the NDT model to increase the input data
accuracy.
b) If the output data accuracy meets the consumer data accuracy requirements, this may indicate that the
accuracy level of the NDT output is meeting the consumer requirements. In such a case the NDT output
may be used with high confidence.
c) If the input data accuracy meets the consumer data accuracy requirements, this may indicate that the
NDT MnS producer is working with the sufficiently accurate data, models and performance for the
service requested.
d) If the output data accuracy is not meeting the consumer data accuracy requirements the NDT MnS
producer is not performing accurately when compared with the same metric or function or behaviour of
the proposed changes in the physical twin. In such a case NDT MnS producer may need to be
reconfigured to improve the performance.
6 NDT for zero-touch Network and Service
management
6.1 Principles
1) NDT should be use case specific
Different use cases will use NDT differently, for example, in the radio network energy saving use case described in
clause 5.1, NDT can serve network optimization service, and in the signalling storm simulation use case described in
clause 5.3, NDT can be used for information prediction. Therefore, the NDT, including the input and output as well as
the data on which the NDT depends, etc. should be use case-specific. NDT may use data from various sources and are
needed to be at right level of granularity, abstraction level, meets the quality, quantity criteria and other data
characteristics (like peak hour KPI) requirements of the use case.
ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
28
2) Different actions in NDT may be executed concurrently
Take the radio network energy save as an example, NDT may be used to verify expected behavioural impacts for
multiple derived actions in this use case (e.g. switch on some energy saving algorithms in the cell, configure the cell
overlaid relations, etc.). Generally, these different actions verification will be implemented in the same NDT. It is
recommended that NDT can be executed concurrently and independently, instead of sequentially, to greatly boost the
processing efficiency.
A particular NDT may serve multiple MnS consumers - i.e. as well as multiple "requests" from the same MnS consumer
- if those consumers require similar analyses and, therefore, the use of similar models and data (this is essentially an
implementation-determined distinction). However, as may be the case with respect to concurrent or serial requests from
a single MnS consumer, various MnS consumers may require analyses corresponding to scenarios that are different in
detail, e.g. with respect to modelling time, network composition or condition, traffic, services, or other factors.
NDTsthus require careful handling of data and models, across parallel and sequential computational sessions, to
accommodate such differences in scenario details.
Parallel computational sessions require managed life cycles. Sessions may be short-lived, e.g. seeking one-time "what-
if" scenario-based predictions; or, they may be long-lived, e.g. seeking continuing modelling as physical twin-sourced
data evolves. Consumers of NDT managed services should control or influence these life cycles.
Depending on the details of scenarios requiring analysis, NDT computational sessions may use data that corresponds
fully, partly or not at all to data representing the current state of the physical twin. However, the latter data should
remain accessible to every session and uncorrupted by its differential substitution with scenario-specific data. I.e.
sessions use and modify the physical network data as a "branch version" and should not modify the original version of
the physical network data.
NDT computational sessions may involve different detailed functional models. For example, scenarios may involve
additions to, deletions from, or other modifications to deployed equipment or other elements. Network functional
models may be generated by composition from atomic equipment or element model instances, thus requiring different
network model compositions across scenario-based sessions. Further, details of functional models invoked may differ
depending on whether the modelled network is fully real - i.e. is fully deployed and potentially operating - or is partly or
fully hypothetical. Functional models may be available corresponding to specific instances of deployed equipment;
otherwise, only equipment type-specific or even generic functional models, presumably of lesser accuracy or quality,
may be used.
3) Separation of Concerns in NDTs
In order to support the separation of concerns in management, described in principle 8 from ETSI GS ZSM 002 [i.6],
clause 4.2.8, the ZSM framework supports the same separation of concerns in NDTs as follows:
• E2ESMD NDT: Provide management services (MnS) and capabilities as described in clause 6.3 which support
the management of end-to-end managed services that span multiple management domains.
• MD NDT: Provide management services (MnS) and capabilities as described in clause 6.3 which support the
management of management domain entities.
4) NDT enables improved decision-making through its dynamic behaviour modelling capability
NDT's dynamic behaviour modelling capabilities like simulation, emulation and prediction enable network and service
management to have improved decision-making capabilities compared to traditional methods without any adverse
impact on the physical twin.
5) NDT is aware of the dynamic changes of the physical twin environment
The NDT is environment-aware based on information received from telemetry data, sensors, anomaly detection, failure
prediction etc. The dynamic behaviour models may be calibrated with the dynamic changes in the physical twin and its
environment.
ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
29
6) NDTs should accommodate reasonable variation in physical twin detailed composition
In practice, NDTs are likely to be required to operate in conjunction with real networks that vary and evolve in a
number of ways, including network size, specific equipment types involved, and available instrumentation or other data
sources, types and quality. These variations affect the types and quality of both available functional models and data
available to feed them. As a rule, the best available models and data should always be used, in optimum combinations,
to generate the best quality model outputs, with choices re-examined based on evolution of available models, data and
target computation scenarios.
6.2 NDT Mapping to ZSM Architecture
6.2.1 Analyzing NDT
When an Analyzing NDT pertains to a management domain (MD) and the entities managed by that MD, the
management services (MnSs) the NDT provides fall within the domain analytics category of MnS described in ETSI
GS ZSM 002 [i.6]:
"The domain analytics services provide domain-specific insights and generate domain-specific predictions based on
data collected by domain data collection services and other data (e.g. data collected by other domains or stored in data
services)".
An Analyzing NDT generally consumes domain data collection services, e.g.: event notification services, performance
measurements streaming services, performance measurements collection services or log collection services, inventory
services, topology services (which are described as part of an orchestration group of services), some basic analytics
services and even control services - e.g. reading certain configuration settings, and possibly intelligence services. As
noted in clause 4.1, the very notion of digital twins is predicated on consumption of these types of services.
The provision of predictive behavioural, functional, performance or similar information is the service - the MnS -
provided by an Analyzing NDT. Domain-level consumers of Analyzing NDT-provided services include providers of
decision making and action planning services, which are described as domain intelligence services in ETSI
GS ZSM 002 [i.6] and may constitute further components of closed loops supporting operations automation. For
example, a designer of optimized network or service configurations, might postulate candidate configurations and then
use the services of an Analyzing NDT to assess their workability, degree of optimality, etc. As this example illustrates,
consumers of Analysing NDT services may play a role in the specification of scenarios for which predictions are to be
delivered by the Analyzing NDT. Scenario specification might involve, for example, the selective modification,
replacement or complementing of data provided to the Analyzing NDT by data collection services.
A consumer of services provided by a domain-oriented Analyzing NDT may lie within the same MD as the NDT, in
another MD or in an E2E MD. Similarly, services consumed by an Analyzing NDT may be generated within the same
MD as the Analyzing NDT, in another MD or in an E2E MD. As per ETSI GS ZSM 002 [i.6], these various scenarios
are enabled by domain integration fabrics, cross-domain integration fabrics, domain data services and cross-domain
data services, as applicable.
An Analyzing NDT may pertain to an E2E MD. An E2E MD-associated Analyzing NDT provides an E2E service
analytics function as per ETSI GS ZSM 002 [i.6]. It may consume e.g. E2E service data collection, domain data, and
cross-domain data services; and its services may be consumed by e.g. E2E service orchestrators.
ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
30
6.2.2 Controlling NDT
A Controlling NDT - one that can drive configuration, provisioning or similar actions on the physical twin - extends the
services provided by an Analyzing NDT with additional management services, particularly those representing
additional closed loop stages. Examples of such services include the intelligence services - decision making and action
planning - referred to above, as well as domain control services, domain orchestration services or E2E orchestration
services that may drive action on the physical network.
6.3 Potential new ZSM Framework Capabilities to support the
NDT
6.3.1 Generic Capabilities
Capability-6.3.1-1: It is recommended that the ZSM framework provides capabilities to integrate the NDT in the
MD/E2ESMD.
Capability-6.3.1-2: It is recommended that the ZSM framework provides capabilities to support the use of NDT
together with the CI/CD pipeline to support continuous testing on the CI/CD pipeline.
Capability-6.3.1-3: It is recommended that the ZSM framework supports the capability to allow an authorized MnS
consumer to request an NDT to provide predictions.
NOTE 1: Examples of predictions may be network performance or network behaviour predictions.
Capability-6.3.1-4: It is recommended that the ZSM framework supports the capability of requesting the NDT to
provide data, models or both to support visualization of use case relevant information to an
authorized ZSM consumer.
NOTE 2: Examples of use case relevant information may be the watts per hour on an energy consumption use case
or the network KPIs on a network prediction use case.
Capability-6.3.1-5: It is recommended that the ZSM framework provides capabilities to support the NDT to
create a digital representation of an E2E communications network or functionality or
service, and its environment or parts of them.
NOTE 3: The expression "E2E" refers to the end-to-end view in ZSM.
Capability-6.3.1-6: It is recommended that the ZSM framework provides capabilities to support the NDT to
assist the continuous deployment of functionalities and services in a communications
network.
Capabiity-6.3.1-7: It is recommended that the ZSM framework provides capabilities to support the NDT to
assist the continuous integration in a communications network.
Capability-6.3.1-8: It is recommended that the ZSM framework provides capabilities to support the NDT to
provide analytics and diagnostics to an authorized ZSM consumer
NOTE 4: Such diagnostics could be related for example to a root cause analysis.
Capability-6.3.1-9: It is recommended that the ZSM framework provides capabilities to support the NDT to
provide recommendations concerning improvements as well as cost savings for network
and service management solutions.
NOTE 5: Examples of network and service management solutions are solutions to increase energy efficiency and
energy savings as well as streamlining processes to increase network and service quality as well as cost
savings.
Capability-6.3.1-10: It is recommended that the ZSM framework provides capabilities to use NDT related
services to support near real-time and real-time operations.
NOTE 6: The definitions of near real-time and real-time is for further study.
ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
31
Capability-6.3.1-11: It is recommended that the ZSM framework provides capabilities for an authorized ZSM
consumer to request tracing of recommendations and/or decisions provided by or enabled
by the NDT in the management context.
6.3.2 Data collection
Capability-6.3.2-1: It is recommended that the ZSM framework can support the capability to collect required
data from managed entities within the ZSM framework to perform automated network and
service management based on the use case the NDT is used for.
NOTE 1: Data here refer to different types of data (e.g. configuration data, historical data, operational data,
performance data, etc., as defined in clause 4.1) which may require different collection frequencies (e.g.
minute-level, 10-second level, second-level, etc.).
As mentioned in clause 4.1, current data specific to the 'real-world' networks they represent is essential for the NDT,
and it is expected that the required current data that can be collected from the 'real-world' network to build and update
the network digital twin is up-to-date. In some cases, the data collection characteristics such as frequency, on demand
mode needs to be configured for NDT.
ETSI GS ZSM 002 [i.6] (clause 6.5.2 and clause 6.6.2) defines data collection services, provide capabilities to monitor
the managed entities and consumed managed service. These services may be enhanced or modified to meet the
requirements of NDT.
Capability-6.3.2-2: It is recommended that the data collection services described in ETSI GS ZSM 002 [i.6]
(clause 6.5.2 and clause 6.6.2) are extended to support the capability to configure the
frequency, method of data collection, or more configuration, based on the usage of NDT.
NOTE 2: An example of collection method is obtaining batches of collected measurements or obtaining streams of
data.
6.3.3 Data Generation
Capability-6.3.3-1: It is recommended that the ZSM framework supports the capability to allow an NDT to
trigger synthetic data generation based on the requirements of the NDT.
Capability-6.3.3-2: It is recommended that the ZSM framework supports the capability to allow the synthetic
data and other collected data to be used in the NDT solution.
NOTE 1: Collected data is described in ETSI GS ZSM 002 [i.6], clause 5.3.2, and it refers to the data from data
collection services.
Capability-6.3.3-3: It is recommended that the ZSM framework supports the capability to allow NDT MnS
producer to trigger the validation of the synthetic data.
NOTE 2: An example of validation method is comparing the synthetic data to the real data from the physical twin.
6.3.4 Historical capabilities
Capability-6.3.4-1: It is recommended that the ZSM framework supports the capability to enable an authorized
NDT MnS consumer to request historical data.
Capability-6.3.4-2: It is recommended that the ZSM framework supports the capability to enable an authorized
NDT MnS consumer to replay historical data as it happened in the network.
NOTE: Replay of the historical data refers to the reproduction of the conditions and events that occurred during
the chosen historical period.
Capability-6.3.4-3: It is recommended that the ZSM framework supports the capability to enable an authorized
NDT MnS consumer to request analysis of what-if scenarios based on variations of
historical events.
ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
32
6.3.5 NDT ML inference-impact emulation
NDT ML inference impact emulation use case is described in clause 5.6. Below are the recommended capabilities:
Capability-6.3.5-1: It is recommended that the ZSM framework can support the capability to allow an
authorized MnS consumer to request and manage an NDT MnS for emulation of ML
inference of an ML entity to analyse the impacts.
NOTE 1: Such request may include inference data characteristics and inference impact emulation characteristics.
NOTE 2: Examples of inference data characteristics may be the data set to be used for the inference or inference
data set characteristics.
NOTE 3: Examples of inference impact emulation characteristics may include traffic pattern (e.g. busy hour),
coverage scope (e.g. urban, rural), trustworthiness, etc.
Capability-6.3.5-2: It is recommended that the ZSM framework can support the capability to allow an
authorized MnS consumer to request reporting on results of emulation of ML inference and
the impacts.
Capability-6.3.5-3: It is recommended that the ZSM framework can support the capability to allow an NDT as
ML inference impact emulator to report results of emulation of ML inference and the
impact.
6.3.6 NDT resource orchestration capabilities
NDT resource orchestration management
use case is described in clause 5.10. Below are the recommended capabilities:
Capability-6.3.6-1: It is recommended that the ZSM framework can support the capability for NDT MnS
producer to process more than one NDT MnS request concurrently and either partially or
fully resource sharing capabilities in order to achieve efficient resources utilization.
NOTE 1: Clause 6.1 describes principle "Different actions in NDT may be executed concurrently".
NOTE 2: Examples of resources may be HW like CPU, storage, RAM etc. or SW.
Capability-6.3.6-2: It is recommended that the ZSM framework can support the capability of NDT resource
management and orchestration service to identify, and manage effective resource utilization
using the NDT concurrent processing and resource sharing capabilities.
Capability-6.3.6-3: It is recommended that the ZSM framework can support the capability for the NDT
resource management to trigger cleanup of unnecessary NDT MnS producer instances
when all the NDT MnS requests associated with that NDT MnS producer instance have
been fulfilled.
6.3.7 NDT Time Management Capabilities
NDT time delay is described in the clause 5.11. Below are the recommended capabilities:
Capability-6.3.7-1: It is recommended that the ZSM framework provides capabilities to configure acceptable
time delay and monitor NDT time delay.
NOTE 1: Examples of NDT time delay related configuration may be acceptable time delay by the consumer.
Capability-6.3.7-2: It is recommended that the ZSM framework provides capabilities to configure and manage
NDT time synchronization with the physical twin time.
NOTE 2: Configuration may specify criteria to trigger NDT time synchronization with physical twin time.
NDT virtual clock and NDT master virtual clock are described in the clause 5.11. Below are the recommended
capabilities:
Capability-6.3.7-3: It is recommended that the ZSM framework provides capabilities to support NDT virtual
clock.
ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
33
Capability-6.3.7-4: It is recommended that the ZSM framework provides capabilities to synchronize time of
one or more NDTs to the same NDT virtual clock.
NOTE 3: The NDT virtual clock to which one or more NDTs synchronize plays the role of NDT master virtual
clock.
6.3.8 NDT consumer preference capabilities
NDT consumer preference use case is described in clause 5.12. Below are the recommended capabilities:
Capability-6.3.8-1: It is recommended that the ZSM framework can support the capability for authorized
consumer to provide its configuration to NDT MnS producer.
Capability-6.3.8-2: It is recommended that the ZSM framework can support the capability for NDT MnS
producer either acknowledge acceptance of configuration requested or provide
recommendations for potential configuration to authorized consumers based on feasibility
check.
Capability-6.3.8-3: It is recommended that the ZSM framework can support the capability for NDT MnS
producer to report about the fulfilment of the configuration requested by authorized
consumers.
6.3.9 NDT Fault injection capabilities
NDT fault injection
use case is described in clause 5.13. Below are the recommended capabilities:
NOTE: These may be optional or specialized capability to generic NDT simulation capabilities.
Capability-6.3.9-1: It is recommended that the ZSM framework can support the capability for authorized
consumer to provide the fault exploration scenarios to NDT MnS producer.
Capability-6.3.9-2: It is recommended that the ZSM framework can support the capability for NDT MnS
producer to explore and simulate potential fault scenarios based on a policy configured or a
fault signature specified by authorized consumers.
Capability-6.3.9-3: It is recommended that the ZSM framework can support the capability NDT MnS producer
to collect and provide the fault signatures to authorized consumers or MnS.
6.3.10 NDT data accuracy capabilities
The NDT data accuracy use case is described in clause 5.14. Below are the recommended NDT data accuracy
capabilities:
Capability-6.3.10-1: It is recommended that the ZSM framework can support the capability to enable an
authorized NDT MnS consumer to request the input and output data accuracy that should
be realized by NDT.
Capability-6.3.10-2: It is recommended that the ZSM framework can support the capability to enable the NDT
MnS producer to report about the input data accuracy to an authorized MnS consumer.
Capability-6.3.10-3: It is recommended that the ZSM framework can support the capability to enable NDT MnS
producer to report about accuracy of the output data from the NDT, compared to the
behaviour of the physical twin at the same time as related to the NDT virtual time to an
authorized MnS consumer.
Capability-6.3.10-4: It is recommended that the ZSM framework can support the capability to enable an NDT
MnS producer to perform actions in order to fulfil the requirements on input or output data
accuracy as requested by the authorized NDT MnS consumer.
NOTE: Example of actions to fulfil input or output data accuracy may be tightening input data synch, examining
the need for model improvement.
ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
34
Annex A (informative):
Change history
Date
Version
Information about changes
May 2022 0.0.1 Initial skeleton for approval
June 2022 0.0.2 Skeleton approved during ZSM Tech Call #19e
February 2023 0.0.3
Added contributions:
• ZSM(22)000391r5_ZSM015_Add NDT scenario signalling storm
• ZSM(23)000019r1_ZSM015_Adding requirements to verification scenario
• ZSM(22)000271r10_ZSM015_Add_benefit of network digital twin
• ZSM(22)000388r3_ZSM015_Section 4.1 Concept of Digital Twin
• ZSM(23)000013_ZSM015 - editing terms and abbreviations
• ZSM(22)000361r4_ZSM015_Add scenario related to risk prediction for network
slicing using NDT
• ZSM(22)000305r4_ZSM015_Add scenario related to verification using NDT
March 2023 0.0.4 Undo the changes made in the draft without approved contribution. zsm#22c tech call
May 2023 0.0.5
Added contributions:
• ZSM(23)000049r1_ZSM015_Editing_terms_and_abbreviations
• ZSM(23)000051_ZSM015_Add_subclause_to_capabilities
• ZSM(23)000044r2_ZSM015 Adding capabilities
• ZSM(23)000062r2_ZSM015_Industry Progress for NDT
• ZSM(23)000016r2_ZSM015_Add_NDT_scenario_ML_training
• ZSM(23)000055r6_ZSM015_Adding_capablities_of_data_collection
• ZSM(23)000077r1__ZSM015 Sec 4.3.2 Digital Twin Industrial Progress
July 2023 0.0.6
Added contributions:
• ZSM(23)000017r5_ZSM015_Add_NDT_scenario_DevOps
• ZSM(23)000047r3_ZSM015_Clause_5_4_ML_inference_Impact_Emulation
• ZSM(23)000071r8_Adding_capabilities_of_data_generation
• ZSM(23)000091r2_ZSM015_Add_principle_of_network_digital_twin
• ZSM(23)000093r2_ZSM_015__New_potential_ZSM_capabilities_to_support_t
he_NDT
• ZSM(23)000102_ZSM015_Changes_in_clause_63
• ZSM(23)000103r1_ZSM015_Changes_in_reference
August 2023 0.0.7
Added contributions:
• ZSM(22)000389r3_ZSM015_Clause_6_2_NDT_mapping_to_ZSM_architecture
• ZSM(23)000129r5_ZSM015_Add_Visualization_Capabilities_
• ZSM(23)000133r2_ZSM015_Network_Playback_use_case
• ZSM(23)000134r4_ZSM015_Network_playback_capabilities
• ZSM(23)000135r4_ZSM015_HIerarchical_NDT_principle
• ZSM(23)000138r3_ZSM015_Add_Prediction_Capabilities
• ZSM(23)000168r2_ZSM015_Editing_terms_and_abbreviations_1
• ZSM(23)000169r2_ZSM015_Editing_terms_and_abbreviations_2
September 2023 0.0.8
Missing one sentence from contribution ZSM(22)000388r3_ZSM015_Section 4.1
Concept of Digital Twin
Added contributions:
• ZSM(22)000279r4_ZSM015_Section_5_Automation_Scenarios_Using_NDT
• ZSM(23)000070r3_ZSM015_Sec_4_1_2_NDT_Taxonomy_Scope_Examples
• ZSM(23)000141r2_ZSM015_Sec_4_3_3_Synergies_between_Industrial_DT_a
nd_NDT
• ZSM(23)000127r8_ZSM015_Sec_5_X_Data_Generation_for_NDT
• ZSM(23)000160r2_ZSM015_Sec_5_X_NDT_resource_management_and_orc
hestration
• ZSM(23)000121r4_ZSM015_Sec_6_3_x_NDT_ML_Inference_Emulation_Cap
abilities
• ZSM(23)000161r2_ZSM015_Sec_6_3_x_NDT_resource_orchestration_capabil
ities
• ZSM(23)000192r2_ZSM015_Changes_in_Section_4_1__NDT_Types_
• ZSM(23)000193r1_ZSM015 Changes in Section 6_2 (NDT Types)
• ZSM(23)000200r1_ZSM015_Sec_6_3_x_NDT_Fault_injection_Capabilities
ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
35
Date
Version
Information about changes
November 2023 0.0.9
Added contributions:
• ZSM(23)000112r8_ZSM015_Sec_4_1_X_NDT_Time_Management
• ZSM(23)000139r4_ZSM015_Sec_6_3_x_NDT_Time_Management_Capabilitie
s
• ZSM(23)000143r2_Adding_capabilities_of_synthetic_data_validation
• ZSM(23)000195r1_ZSM015_Sec_5_X_NDT_consumer_preference
• ZSM(23)000196r1_ZSM015_Sec_6_3_x_NDT_consumer_preference_capabilit
ies
• ZSM(23)000199r2_ZSM015_Sec_5_X_NDT_Fault_Injection_Analysis
• ZSM(23)000200r1_ZSM015_Sec_6_3_x_NDT_Fault_injection_Capabilities
• ZSM(23)000213_ZSM015_Editorial_changes_on_section_4_and_section_5
November 2023 0.1.0
Added contributions:
• ZSM(23)000094r5_ZSM_015__Additional_new_potential_ZSM_capabilities_to
_suppor
• ZSM(23)000095r4_ZSM_015__Further_new_potential_ZSM_capabilities_to_s
upport_t
• ZSM(23)000096r3_ZSM_015__One_additional_new_potential_ZSM_capability
_to_supp
• ZSM(23)000178r1_ZSM_015__Additional_new_potential_ZSM_capabilities_to
_suppor
• ZSM(23)000179r1_ZSM_015__Additional_new_potential_ZSM_capabilities_to
_suppor
• ZSM(23)000190r2_ZSM015_Section_4_4_Emulation__Simulation_and_Modell
ing_Time
• ZSM(23)000207r2_ZSM015_NDT_Prediction_principle
• ZSM(23)000221r1_ZSM015_Editorial_changes_on_section_5
• ZSM(23)000222r1_ZSM015_Changing_figure_of_5_2_2
• ZSM(23)000247r1_ZSM015_Sec_6_1_NDT_environment_aware_principle
• ZSM(23)000251r1_ZSM015_Sec_6_1_NDT_should_be_use_case_specific
December 2023 0.1.1
Added contributions:
• ZSM(23)000122r10_ZSM015_Sec_5_X_NDT_data_drift
• ZSM(23)000123r6_ZSM015_Sec_6_3_x_NDT_data_drift_capabilities
• ZSM(23)000211r2_NDT_Data_and_Model_Management
• ZSM(23)000260_ZSM015_Editors node clause 1
• ZSM(23)000261_ZSM015_Removal of ENs
• ZSM(23)000262_ZSM015_Editors note clause 4.2
• ZSM(23)000263r1_ZSM015_Editors note clause 5
January 2024 0.1.2
• Formatting changes
• Keywords

ETSI
ETSI GR ZSM 015 V1.1.1 (2024
-
02)
36
History
Document history
V1.1.1 February 2024 Publication
